The increase in prevalence and sophistication of cyber attacks in recent years is undeniable and according to the IBM Cost of a Data Breach Report 2020, the shift to remote working during the global pandemic increased the average cost of a data breach by $137,000 bringing to average total cost to $4 million.
This rise is believed to be due to the lack of endpoint security employees have at home compared to the levels of protection they would have in the office.
IBM’s report also found that more than half (52%) of breaches were caused by a malicious attack, and one in five companies that suffered a breach was as a result of stolen or compromised credentials.
Organisations of all sizes are vulnerable
Once considered a concern for only large companies, recent research from Cybint showed that 43% of cyber attacks target small businesses. But that does not mitigate the threat to large companies, as the recent attack on supermarket giant Tesco proved.
Customers began reporting issues with the Tesco website and app on the 23rd October with many unable to use the search function, make or cancel orders or amend their scheduled deliveries. Tesco later announced that there had been an attempt to interfere with Tesco systems’ but there was no reason to believe that customer data had been impacted.
The disruption continued until the evening of the 24th October, with the retailer announcing that the grocery website and app were back up and running with a temporary virtual waiting room in place to help manage the heightened demand.
Managing the cyber risk
Despite the ever-expanding attack surface and growing threat landscape, a recent McKinsey survey found that only 16% of executives say their organisations are well prepared to deal with cyber risk with many executives saying they find it challenging to keep up with cyber risk management.
As the risk continues to grow and threat actors continue to use more advanced techniques, IT security planning should be a priority for businesses of all shapes and sizes and across all industries.
A managed SIEM solution for example is a critical defence tool for protecting any business, providing a single view of your IT security and our free OTX Endpoint Security tool, powered by MTI partner AT&T’s AlienVault Agent, allows organisations to assess if endpoints have been compromised. But how can the NIST Cybersecurity Framework help improve an organisation’s security posture?
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a set of guidelines and best practices set out by the National Institute of Standards and Technology (NIST) to provide a uniform set of rules and standards for organisations across all industries to follow.
The framework is a powerful tool that is designed to help organisations improve their cyber security posture by enabling them to be better prepared in identifying and detecting cyber attacks, and sets out recommendations on how to respond, prevent and recover from breaches.
When it comes to IT security planning and building a cyber security programme, the NIST Cybersecurity Framework is widely considered the gold standard and can help organisations develop a robust security plan.
5 core functions of NIST Cybersecurity Framework
The framework consists of five core functions to help categorise all cyber security capabilities, projects, processes and daily activities. There are broken down into:
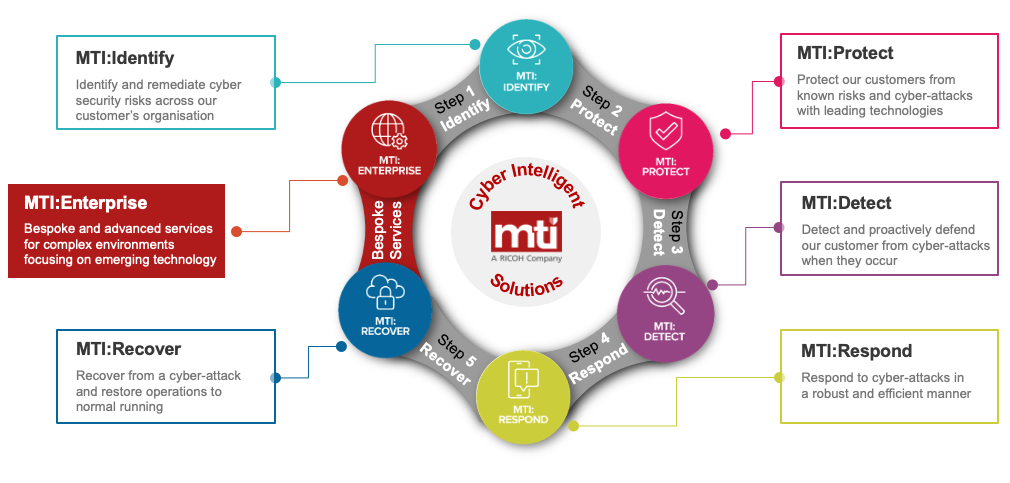
Identify
The identify function focuses on laying the groundwork to create an effective cyber security program by helping organisations understand their risks and what needs protecting. Essential activities include:
- Identifying the physical and software assets as a basis of an asset management program.
- Identifying the organisation’s business environment and its role in the supply chain.
- Identifying established cyber security policies to define governance and highlight legal and regulatory requirements.
- Identifying asset vulnerabilities, threats to internal and external resources and risk response activities to help assess risk.
- Developing a risk management strategy and identifying risk tolerance.
- Understanding the supply chain risk and developing a management strategy.
Detect
The detect function enables organisations to define the activities to detect a cyber security event in a timely manner, including:
- Ensuring anomalies and events are identified and their potential impact is understood.
- Implementing continuous monitoring capabilities to monitor security events and verify the effectiveness of protective measures that have been put in place.
Respond
The respond function highlights the activities to take in the event of a cyber security incident is detected, including:
- Executing response planning processes during and after an incident.
- Managing communications with internal and external stakeholders during and after an incident.
- Through analysis of the incident, including forensic analysis to ensure an effective response, determine the impact and support recovery activities.
- Actioning mitigation activities to contain the event and resolve the incident.
- Taking learnings from the event to implement improvements to the security plan and review existing strategies.
Recover
The recover function helps identify plans for resilience and restore any capabilities or services that were impaired during the incident. Essential activities in the recover function are similar to those in the response function, including:
- Implementing recovery planning processes and procedures to restore systems and assets impacted by the cyber security incident.
- Managing communications with internal and external stakeholders during and after an incident.
- Taking learnings from the event to implement improvements to the security plan and review existing strategies.
Overcoming challenges with NIST Cybersecurity Framework
With many executives saying they find it challenging to keep up with cyber risk management, the NIST Cybersecurity Framework leverages the learnings from organisations that have addressed cyber security challenges to help organisations better manage their risks, inform their cyber security decisions and prioritise cyber security investments.
It can also help organisations determine the maturity of their cyber security program and provide a framework for conversations with stakeholders, senior management and the board of directors when developing IT security planning.
Next Steps
As a highly experienced and multi-award-winning technology services and solutions provider, MTI is a dedicated data and cyber security specialist. We recognise the need to provide a portfolio of services and technology expertise to help our customers address their cyber security challenges.
By working alongside our customer’s project teams and leveraging our knowledge and service portfolio, organisations can address these challenges and identify, assess, mitigate and respond to the risks they face. Get in touch with us to discuss your requirements with one of our cyber security experts.

