MTI Cyber Design & Deploy Service Areas:
Testing/Assurance
Firewall
SIEM
PAM
Cloud & Office 365
DLP/ Encryption
Email/Web/DNS
EndPoint
Modern, Efficient and Secure
Before designing and deploying a cyber security solution, we initially recommend conducting a thorough assessment to identify potential vulnerabilities, evaluate the value of your digital assets, and assess the impact of a security breach. This forms the foundation for tailoring your cyber security strategy to your specific needs.
Once you’ve identified known risk, we then discuss appropriate solutions to help protect against that risk.

Why MTI?

35 Year Pedigree
As a founding member of global cyber security body, CREST, we have developed a deep understanding of the tactics employed by malicious users to infiltrate corporate networks, allowing us to identify and mitigate any risks to your business.

Unrivalled Expertise
Our professional services team can swiftly and effectively implement remediation measures to ensure your organisation is fully protected.

Tailored Solutions
Whether your infrastructure is on-premises or in the cloud, MTI’s expertise is at your service to keep your business safe and secure.

Increasing Cyber Resilience
MTI has reviewed and improved thousands of cyber security network infrastructures, systems, and solutions. Our expertise can be applied to enhance existing solutions or design secure and resilient cyber security solutions from the ground up, adhering to all relevant industry guidelines and meeting specific project requirements.
MTI’s engineers are trained to efficiently and effectively deploy all supported products. We follow the Prince2 methodology for project management on large-scale deployments and have completed hundreds of referenceable small deployments as well. Our dedicated Project Management Office can support you from design planning to project sign-off, ensuring the security of your business data.
Our Design & Deploy Process
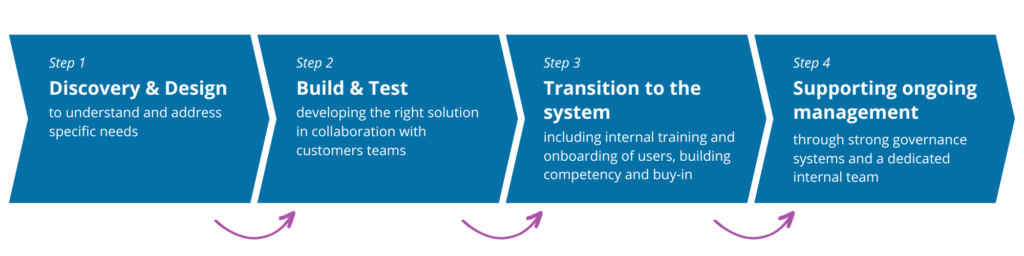
Our Design and Deployment Service in action:

It‘s a pleasure to work with SMEs who know products inside out, and can provide authoritative, clear and comprehensive responses to questions and challenges.
Technical Design Authority Lead
Central Government Department

End-to-End Cyber Security Solutions
Our top-tier partnerships delivering best in class protection for your organisation