Like many people, I’ve been conditioned to be cautious when receiving unexpected emails about financial transactions. But recently, I received an email that initially had me alarmed. The subject line read: “You sent a £399.99 GBP payment.”
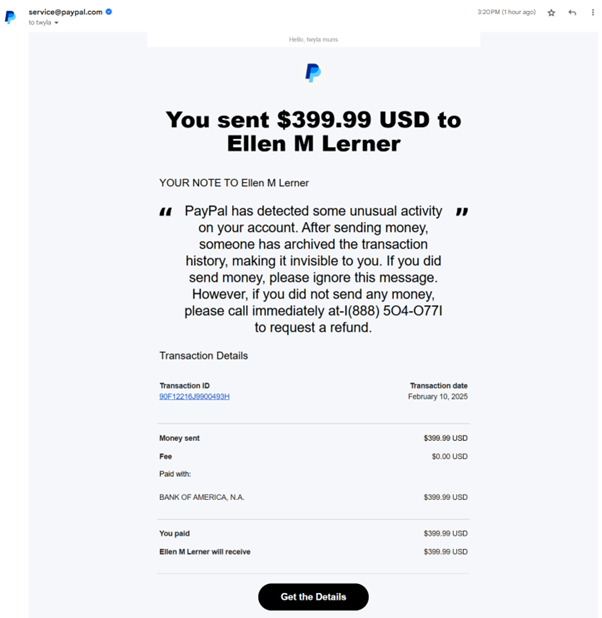
Naturally, my first instinct was concern. I hadn’t authorised any such transaction. As I scanned the email, everything seemed to check out:
- The sender was service@paypal.com.
- The embedded links appeared to be legitimate PayPal URLs when I hovered over them.
- SPF, DKIM, and DMARC authentication all passed, confirming that the email truly came from PayPal’s servers.
Despite all of this, I still didn’t trust the email outright. Instead of clicking any links, I followed best security practices: I opened a new browser tab, manually typed in PayPal.com, and logged into my account to check my transaction history.
Sure enough, there was no record of a £399.99 payment to “Ellen M Lerner.”
At this point, my curiosity kicked in. If the email was genuinely from PayPal, how was it being used for phishing? What was the scammer’s endgame?
Breaking Down the Scam
After carefully reviewing the email headers, I confirmed that the email had indeed originated from PayPal’s infrastructure. But one detail stood out – the phone number included in the message.
“If you did not send any money, please call immediately at I(888) 5O4-O77I to request a refund.”
At first glance, this looked like a standard PayPal support number. But something was off, the phone number contained letter ‘O’s and ‘I’s instead of zeros and ones – a subtle but intentional deception.
How This Scam Works
After piecing together the clues, I realised the attackers had used a clever and dangerous strategy:
A legitimate PayPal account (possibly belonging to another victim) had been compromised.
The attacker set up email forwarding on the compromised account to target new victims.
They initiated a small transaction, possibly to another attacker-controlled account, and inserted a malicious message into the transaction note.
Because PayPal automatically includes transaction notes in email notifications, the phishing message appeared to come directly from PayPal.
Victims panic upon seeing an official PayPal email and call the number listed.
The scammer, posing as PayPal support, tricks victims into providing their login credentials—compromising even more accounts.
Why This Is So Dangerous
This scam is especially effective because it exploits the trust that both users and email security systems place in legitimate senders like PayPal. Unlike traditional phishing attempts:
The email passes all security authentication checks (SPF, DKIM, DMARC) because it originates from PayPal.
The links point to real PayPal URLs—there’s no need for a fake phishing site.
The scam doesn’t require a spoofed email address or fake domain.
Instead, the malicious payload is hidden in the transaction note, making it far more difficult to detect and block.
A Growing Trend: ‘Living Off the Land’ Phishing
This technique aligns with a recent trend in phishing attacks where cybercriminals abuse legitimate platforms to distribute phishing content. Sublime Security recently reported a similar abuse of DocuSign for credential phishing (read their report here).
By leveraging trusted services, attackers bypass traditional security measures and deceive even cautious users who verify sender addresses and links.
How to Protect Yourself
To stay safe from attacks like this, follow these security best practices:
Never trust email links—even from legitimate senders. Always log in manually through your browser.
Look for subtle red flags, like manipulated phone numbers that replace numbers with letters.
Be skeptical of urgency—scammers rely on panic to get you to act before thinking.
Report suspicious messages to the platform being abused (e.g., phishing@paypal.com)
Enable Two-Factor Authentication (2FA) to protect your accounts from unauthorised access.
This experience was a stark reminder of how sophisticated phishing attacks have become. Cybercriminals are constantly finding new ways to exploit trusted services and evade detection. The best defence is a mix of technical security measures and user awareness.
At MTI, we specialise in proactive cybersecurity solutions to help businesses stay ahead of evolving threats. If you want to learn more about how to protect your organisation, contact us today.
Have you encountered similar phishing attempts? Share your experience in the comments below! Let’s help each other stay ahead of these evolving scams.

