With up to 80% of IT security breaches being due to compromised credentials and with privileged accounts existing within almost every organisation, Privileged Access Management (PAM) has become a priority for organisations of all types and sizes.
Building a solid foundation to manage privileged accounts empowers organisations to become more scalable and flexible when adopting new technologies and is critical to protect sensitive information from attack. Effective PAM ensures that only authorised users have access to data and systems.
With many different platforms and PAM service providers on the market, it can be confusing to know what to look for and how you can ensure you partner with the supplier that is best suited to your needs and organisation. Managing and optimising PAM solutions is complex, resource intensive and requires specialist skills.
Our buyers guide to PAM aims to help remove some of the confusion and arm you with the information you need to ensure you are making an informed decision when choosing your PAM partner.
Understanding the threat
Growing dependence on technology and expanding networks have made IT security a much more complex in recent years. Changes in the way we work, such as remote working and BYOD means that organisations don’t just have to make sure their hardware and software is secure, they need to ensure their employees’ devices are also protected.
This coupled with sophisticated hacking techniques such as Man in the Middle and Pass the Hash attacks allow hackers to infiltrate organisations under the guise of an authorised user. As they appear as an authorised user, their presence can go undetected for weeks or even months, given them all the time they need to spread malware and steal valuable information.
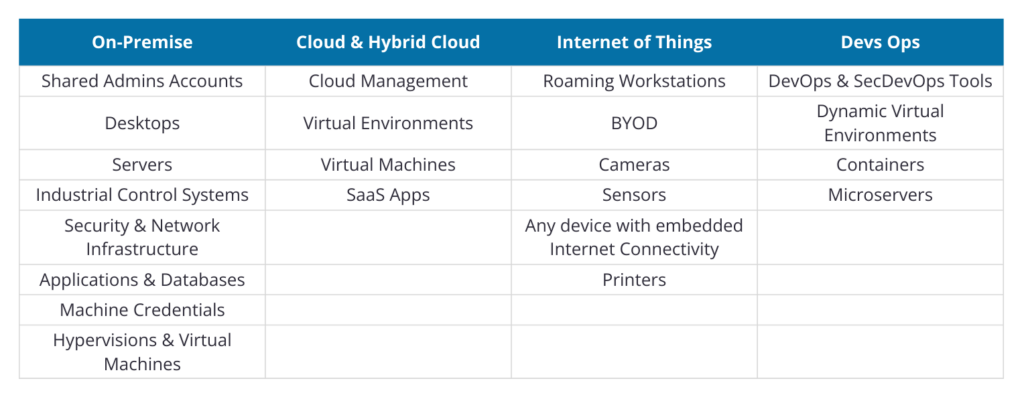
When it comes to PAM, one of the first steps you want to consider is where the threat to your organisation may be. The table below shows the expanding privilege threat surface.
Questions to ask your PAM service partner
When researching your trusted PAM partner there are some basic fundamental principles of PAM that you should consider when speaking to potential suppliers. You want to make sure you are choosing a partner that is well suited to your organisation, meets all of your requirements and provides a holistic approach that covers people, processes and technology.
Below are some questions you may want to consider asking potential suppliers before choosing your PAM partner.
- Will you support us to include privileged accounts in our broader IT cyber security policy?
- Can you help us discover privileged accounts in our organisation automatically?
- Can your solution help us generate complex passwords which are rotated on a regular basis for our privileged accounts?
- Where are the privileged credentials stored? How secure is it?
- Does your system use multiple credential verification?
- What security controls are applied to privileged accounts?
- Does your solution ensure compliance with relevant regulations?
Choosing a partner for your PAM solution
Implement a comprehensive PAM solution with a trusted partner to help you improve IT security, control access to systems and sensitive data, comply with policies and regulations and protect your organisation.
Look for a PAM solution that automates the identification and understanding of risk to your privileged accounts, continuously monitors your environment and provides recording and secure storage.
Thycotic is the leading provider of cloud-ready privilege management solutions. Thycotic’s security tools empower over 10,000 organisations from small businesses to the Fortune 500, to limit privileged account risk, implement least privilege policies, control applications and demonstrate compliance.
Next Steps
A study by Thycotic found that more than 20 percent of organisations do change default passwords, such as “admin” or “12345”. Default passwords combined with the same password being used across multiple accounts is one of the biggest factors that can leave privileged accounts vulnerable to attack.
Protect your organisation against these vulnerabilities today. Contact MTI to discuss how our cyber security services can help strengthen your privileged account security and safeguard your organisation against cyber threats.

