Become Less Reactive in Your Cyber Strategy
Today, the threat landscape and the constant pressure to manage resources effectively means addressing the risks tied to legacy applications and technologies while maintaining a balance between security and usability is paramount. It’s crucial to align your cyber and data strategies to safeguard critical information assets.
This is where our Security Target Operating Model (STOM) methodology comes in. It’s your blueprint to navigate the ever-evolving Cyber Threat landscape, ensuring your business stays resilient and secure in the face of modern threats.
Undertake a Holistic Review of Your Cyber Posture and Hygiene

Cyber Research Centre:
Staffed by our team of Cyber & Data Centre experts, we actively analyse testing data, industry alerts, vulnerability trends and more to feed into the remediation guidance and cyber security maturity roadmaps we develop for our customers.

Insights
Cutting edge insight and analysis on emerging cyber threats and vulnerabilities that enable us to adapt and better protect our customers IT environments.

Innovation
Influences the development of innovative solutions, strategies and technologies to enhance cyber security and protect critical information infrastructure.

Knowledge
Research uncovered is used as knowledge-sharing between our customers and partners.

Action
Provides actionable insights, recommendations, and tools to mitigate cyber risks and strengthen the resilience of organisations against cyber attacks.

MTI has played a crucial role in shaping our Cyber Resilience Strategy, previously we felt we were being very reactive. With the volume of work coming in and the ever-evolving threat landscape, we recognised the urgent need for a more structured and comprehensive strategy. With their expertise and guidance, the MTI team brought a panoramic view of the NHS, enabling us to grasp the bigger picture. They not only provided valuable insights into the national agenda but also ensured our alignment with it— a luxury we simply couldn’t afford to pursue independently. Thus, MTI stepped in, and we are delighted with the results of our collaboration on the cyber strategy. The feedback from everyone has been overwhelmingly positive, impressed by the accomplishments we have achieved together.
Mark Caines
Associate Director of ICT, Digital & Logisitics, ESNEFT

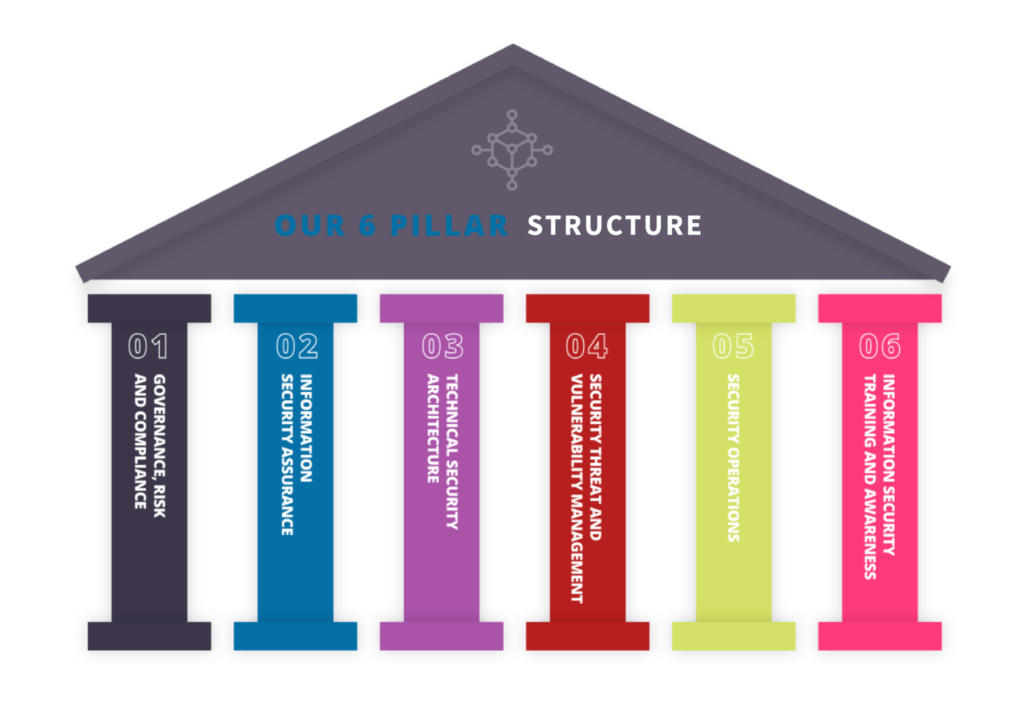
End-to-End Cyber Security Solutions