Our Cyber Security Sourcing Approach
We consistently aim to provide exceptional value to our customers by leveraging our extensive portfolio, which not only includes traditional procurement solutions but also emphasises a strong focus on cutting-edge cyber security services and solutions. Our strong relationships with top manufacturers and specialised cyber security solution providers enable us to secure critical accreditation’s and negotiate better discounts for our customers, ensuring that they receive top-tier protection at the best possible value.
Our expert procurement team excels not only in competitive tendering but also in identifying and integrating the latest cyber security technologies tailored to safeguard your business assets.
We believe in proactive collaboration to identify vulnerabilities and implement strategic defences that align with your business objectives and regulatory requirements. Whether you’re looking to enhance your existing cyber security measures or to build a resilient defence from the ground up, our team is equipped with the expertise and resources to help you achieve a secure and compliant digital environment. Trust us to be your partner in navigating the complex landscape of cyber threats and securing your business’s future.
Recognised on Public Sector Frameworks
MTI is an authorised hybrid infrastructure supplier on many public sector frameworks. We provide our customers with a streamlined procurement process, enhanced compliance and governance, and reduced administrative burden by taking advantage of established contractual terms and conditions and pricing structures.
Our dedicated team, comprised of experienced account managers, technical specialists, and highly qualified security consultants, specialises in offering sustainable, robust cyber security data solutions tailored to the unique needs of a diverse clientele, including Private Sector businesses, NHS, Local, and Central Government entities. We understand that protecting your business against cyber threats is paramount.
Therefore, our approach involves a comprehensive assessment of your current security posture, followed by the implementation of bespoke solutions designed to fortify your digital defences effectively.
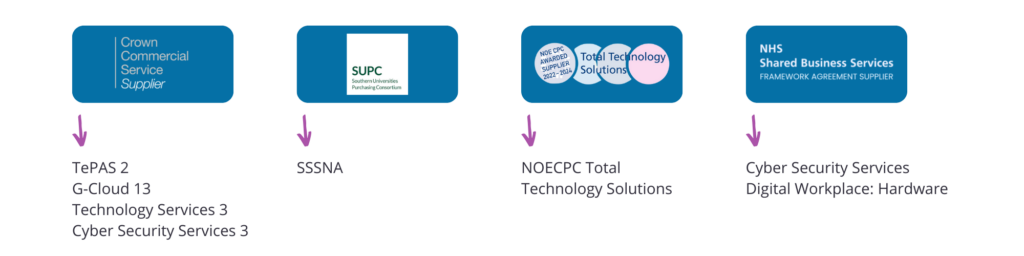
Our top-tier partnerships delivering best-in-class protection for your organisation